Any breach of the Data Security Policy must be reported as soon as possible by telephoning or emailing the Service Desk. Incident are recorded using the Incident Log.
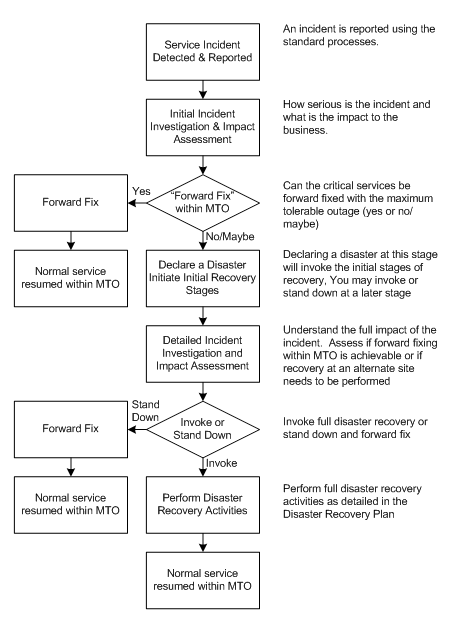
Incident Management
When an incident is reported and entered into the logging system, an email is generated and sent to the Information Security Manager and also copied to the Directors.
All parties dealing with security incidents shall undertake to:
analyze and establish the cause of the incident and take any necessary steps to prevent recurrence
report to all affected parties and maintain communication and confidentiality throughout investigation of the incident
identify problems caused as a result of the incident and to prevent or reduce further impact
contact 3rd parties to resolve errors/faults in software and to liaise with the relevant personnel to ensure contractual agreements and legal requirements are maintained and to minimize potential disruption to other Company systems and services
ensure all system logs and records are securely maintained and available to authorized personnel when required
ensure only authorized personnel have access to systems and data
ensure all documentation and notes are accurately maintained and recorded and made available to relevant authorized personnel
ensure all authorized corrective and preventative measures are implemented and monitored for effectiveness
All incidents logged shall have all the details of the incident recorded - including any action/resolution, links or connections to other known incidents. Incidents which were initially resolved but have recurred will be reopened or a new referencing the previous one will be created.
The Information Security Manager is initially responsible for handling security incidents and will make a decision as to whether an incident needs to be 'handed' over and dealt with by Company Directors where appropriate.